Shared user account#
The general guideline for user accounts at DKRZ is that each user has one individual user account to access the resources we provide.
In rare cases it may be required to share an account among a group of users. The most common cases are large production runs where users take turns in supervising production jobs. It is then required to manage jobs which have been submitted by a different user. Since our scheduler does not allow this with non-administrative accounts, the group of users conducting these production jobs may use a shared user account.
Creating a shared account#
Please contact support@dkrz.de in advance so we can work out whether a shared account is really required for your particular project.
Once this is established, we will create a shared account and assign your main user account as guardian. You have to provide a new email address for the shared account through which we can reach all potential users of the shared account. Note that this cannot be the email address of an existing user account at DKRZ.
Responsibilities of the guardian user#
You as guardian will be responsible for the shared account. Its password can be shared among the group if this is required for accessing certain resources. If SSH login is possible for all required resources, sharing of the password is discouraged, though.
If the password is shared, access to the shared account on https://luv.dkrz.de should be restricted to the guardian user with a FIDO2 hardware key.
Regardless of password sharing or not, the guardian must register all user accounts in the group with access to the shared account on this page
https://luv.dkrz.de/shared-accounts/
Once users have been authorized for access, they can register SSH public keys for the shared account. For each newly registered key, the guardian will receive an email. Since registered keys must be pushed to LDAP, the guardian will have to do this using the shared account.
Group access#
Account sharing is possible only with users who own a regular active user account at DKRZ and who have accepted our guidelines for use.
The preferred way to access the shared account is by installing an individual SSH key for each user. The same lifetime limits for the keys apply as for normal user accounts. For longer key validity we recommend OpenSSH ed25519-sk keys which work with FIDO2 hardware keys.
All users in the group can select the destination user when they upload a new SSH key. For the shared account, the respective guardian will push the keys to LDAP.
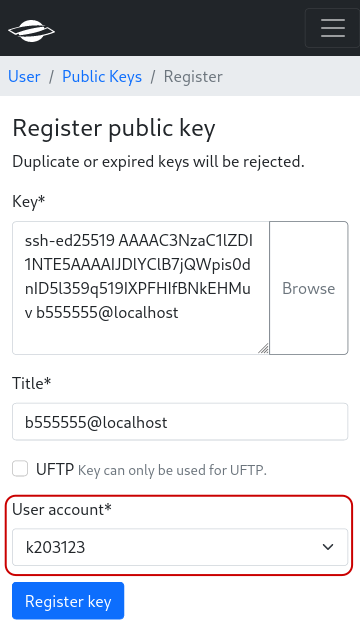
Key registration: Select destination user for public key. This option is only available for users with access to a shared account.#