Multi-Factor Authentication (MFA)#
Multi-Factor Authentication (MFA) enhances security by requiring a one-time password (OTP) token, in addition to a username and password, for logging into various services. This additional verification step helps protect against unauthorized access and strengthens overall account security. The token is generated at the time of login and can be obtained using three different methods:
Authenticator App
Email
Passkey
Configuring OTP-Token#
Log into your user account at the DKRZ user management portal:
Note: If you have already set up a token method, you will be prompted to provide a token for the DKRZ user management portal login.
Navigate to the Tokens section via the user menu at the top right and select
Tokens:
Register a new token method by clicking on
Enroll new token. In the drop-down menu, choose the method for token generation: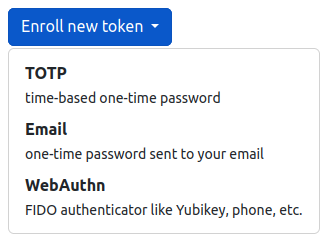
TOTP: Continuously generated temporary OTP (TOPT) token via apps like “Google Authenticator” (Android/iOS) or “WinAuth” (Windows).
Email: A separate email with a token will be sent to you upon each login.
Passkey: Authenticate via a hardware key or protected secret keys, such as fingerprints or Face ID.
TOTP Token#
Note: Before registering a new TOTP token, you may be prompted to re-enter your password. In the first step of the TOTP token configuration, provide a description. As multiple TOTP tokens can be registered, it is useful to add a description based on the app or device the TOTP is registered on, e.g., Google Authenticator App.
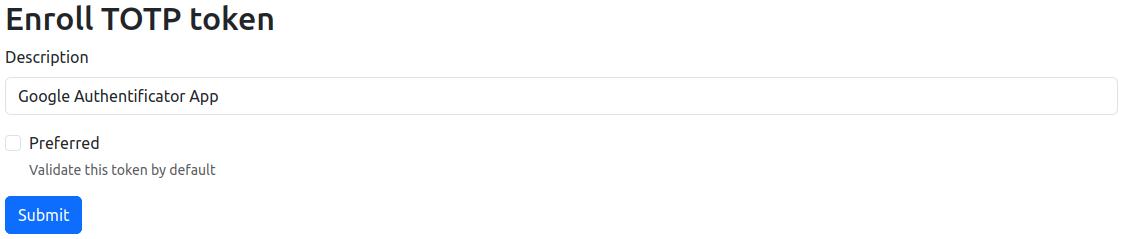
You can set a token as the preferred token, making it the default method during login.
After confirming the information via the Submit button, a QR code and secret will be shown.
Depending on the authentication app, either scan the QR code or enter the secret in the app to add the associated account.
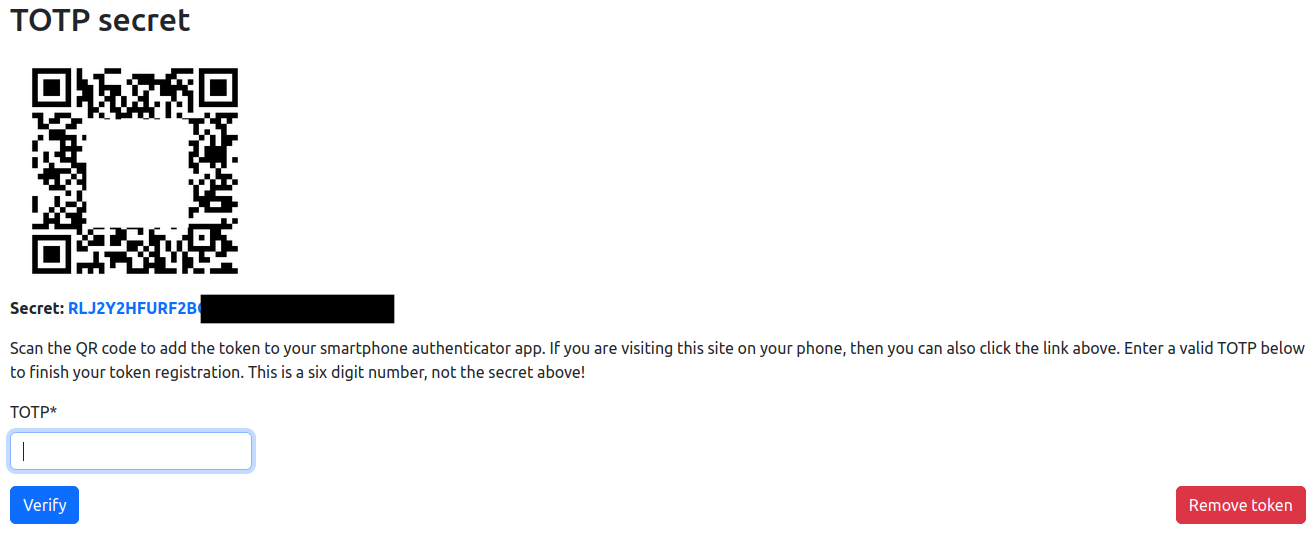
After adding the TOTP (by scanning the QR code or entering the secret) to your app,
a new entry with the name eduMFA: TOTP***** should be visible with a 6-digit key that changes over time.
Enter one of the temporary keys displayed by the app in the TOTP field (see figure above) and then click on Verify to register the app.
Now the changing TOTP keys in the app can be used for MFA authentication in the SSO process of various DKRZ services.
Email Token#
Note: Before registering a new Email token, you may be prompted to re-enter your password. The first token setup via email always uses the existing email address in the DKRZ LDAP system. Additionally, a separate description can be specified for each email:
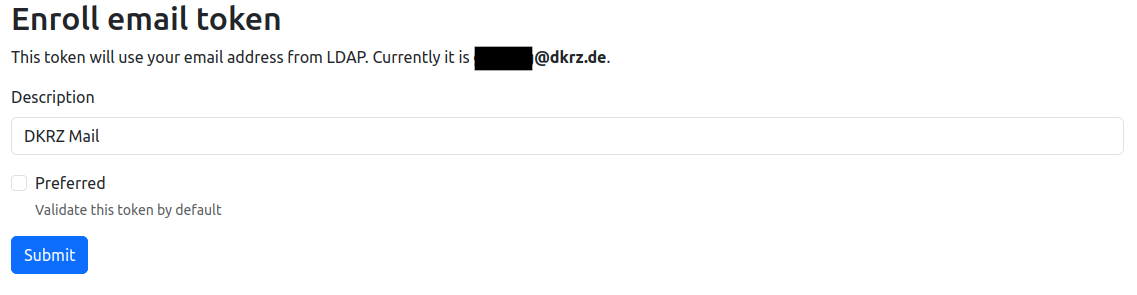
Click Submit to register the LDAP email.
After registering the LDAP email, you can register one more email address as a backup. Enter a user-defined address and description for the second email:
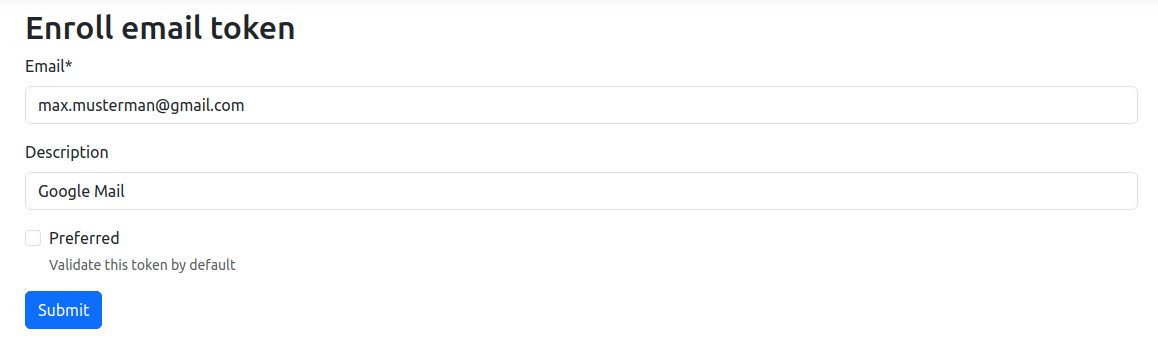
Click Submit to register the second email.
Passkey#
Passkeys allow authentication using a hardware key (e.g., YubiKey), other protected secret keys in a TPM, or using fingerprint or Face ID. The exact registration procedure depends on your operating system and device. Once registered, you can use the key during login by, for example, touching the button on your YubiKey when requested.
To register a hardware key on Windows, plug the key into a USB port on your computer. To enroll the key, click “Enroll new token” and select “Passkey”. Enter a description for the key. The registration process will then begin.
First you have to enter the PIN for the key. You may also have to confirm two warnings before the actual registration occurs.
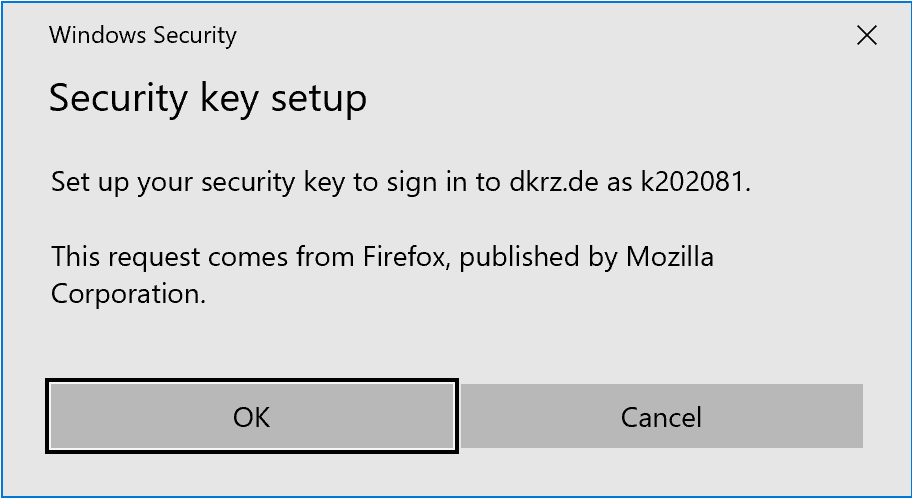
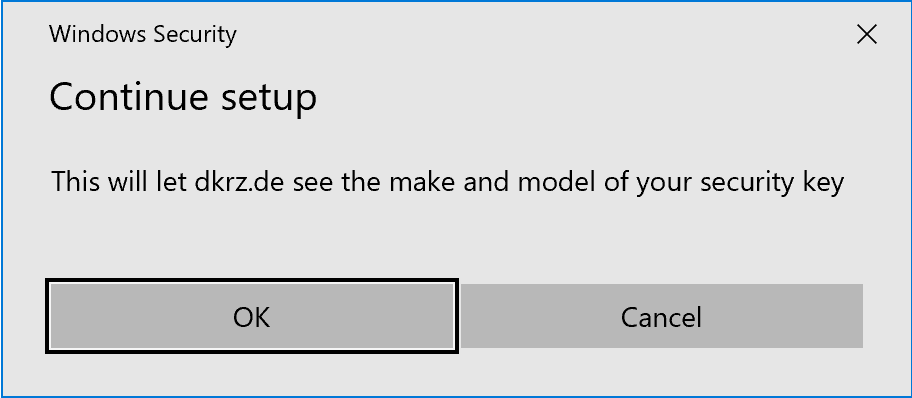
Press the button on the key when asked. It should be blinking.
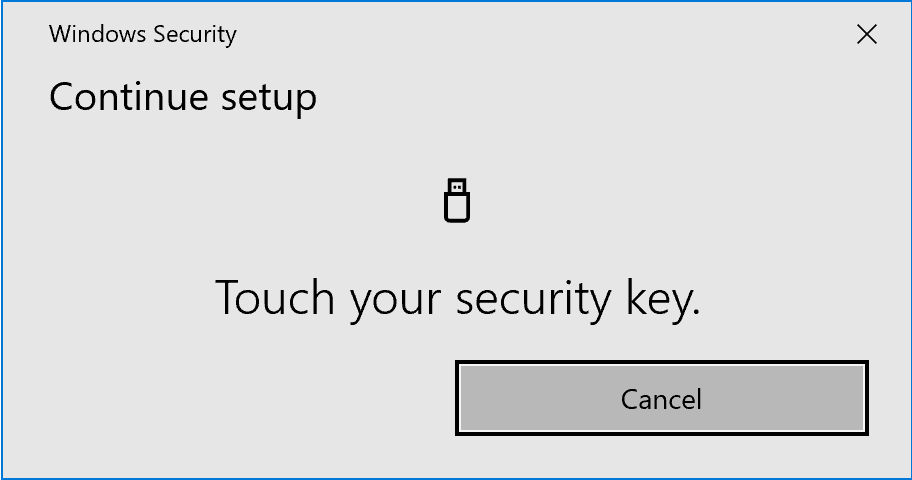
Now the key should appear in the list of tokens.
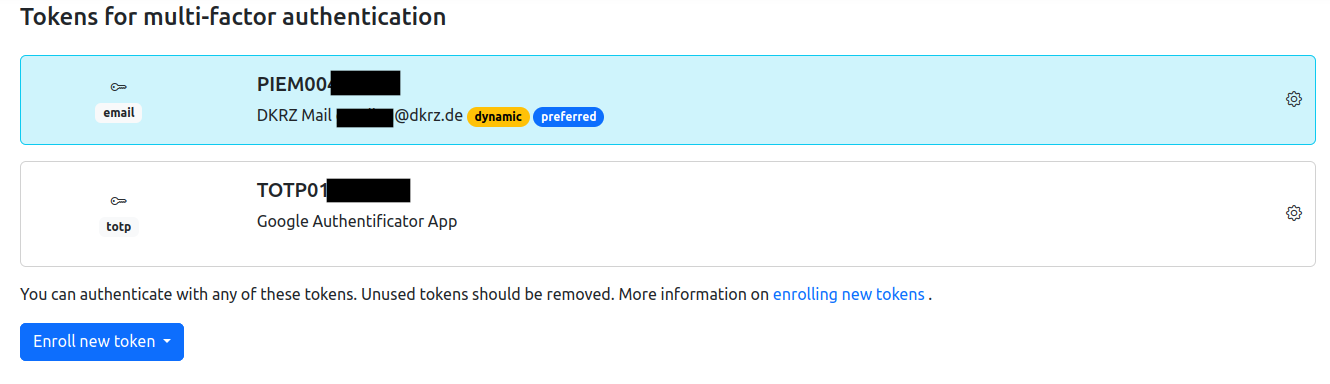
Token Overview#
After adding one or multiple methods for the token, the Token menu should display them:
Note: If you encounter any issues or need assistance, please contact support@dkrz.de.